I have been working on Azure Infrastructure Services since it was in preview release. One of the requirements I was working with was hybrid scenario where VPN between on-premises servers and Azure VMs was essential. Since I was doing all the required testing in my lab at home office, I did not have infrastructure you would usually find in corporate datacenters. I didn’t have a need to buy expensive routers and servers for testing I was doing.
Looking at Azure VPN requirements, you will notice that Windows RRAS is one of the known compatible device. However, all references I found talks about Internet interface of RRAS server must be a public IP address and can’t be behind a NAT router. I did try anyway only to fail.
So I turned my attention to other VPN devices. Again referring to requirements, it was important that the VPN device supports not only Site-to-Site VPN, but must also support AES encryption. I found Netgear FVS318 which was about the cheapest alternative I can find that seem to have met all Azure listed VPN requirements. It didn’t have to be supported device in my case. So I just have to try it and see if it works.
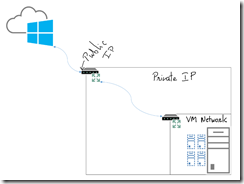
Let’s start with my network. Here’s what it looks like:
Lot of home or even small business networks look something similar to mine. You have a single router provided by cable provider or ISP. It usually is basic NAT router with single public IP on external interface and private IPs on internal interface. It is important to mention that to keep it less complex, I did get two static IP addresses from my ISP. One for all home traffic going to internet which will be using one IP and second IP will be dedicated to Azure VPN. The problem of single NAT router still remained as the router wasn’t advanced enterprise class router and didn’t have capability to allow public IP addresses on the “inside”. The only option I had was to use VPN device on the 192.168.2.x range and have 1:1 NAT using dedicated second public IP.
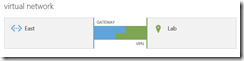
My Lab running in Hyper-V was further isolated on its own subnet so I used new Netgear device to connect the lab for purpose of VPN.In essence, here’s what my network looks like:
Public IP – ISP router – 192.168.2.x – Netgear – 192.168.101.x
Now that basics are out of the way, let’s look at how I went about configuring it.
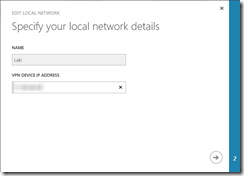
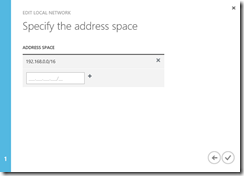
First of all, I created a local network in Azure portal, where I defined VPN Device IP (my public IP) and my VM network (ignore /16 subnet mask, I did it intentionally instead of /24):
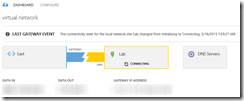
At this point, I needed patience as Azure created gateway for me. When complete, the network dashboard looks similar to this:
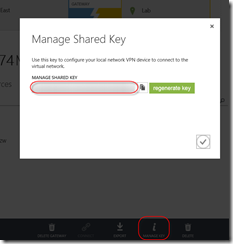
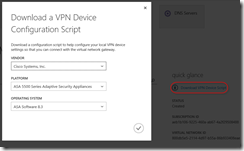
Before I can setup VPN device, I needed to gather a bit more information. I needed shared key and just because I wasn’t familiar with all needed settings, I also chose to download VPN device script even though it wasn’t going to be for my device.
To get the key, click ‘Manage key’ icon at the bottom of network dashboard page I mentioned above. You can simply copy the key to clipboard for configuration later.
For VPN script, the link is to the right on the same page:
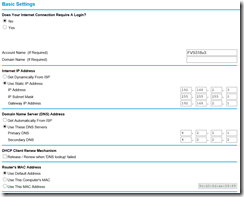
I now had needed information to setup my VPN device. Let’s head over to Netgear configuration user interface. First thing I had to do was define two interfaces. the “internet” interface was on 192.168.2.x network, and since it’s my home network private IP addresses, I assigned a static IP from that range. Basic settings looked something like this:
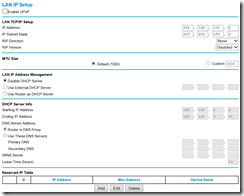
On the “LAN” interface of router, I assigned IP address from my Hyper-V VM Network 192.168.101.x. I didn’t need DHCP on that network so I disabled it. The LAN Setup page looks something like this:
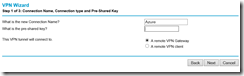
At this point, I am ready to setup VPN. There is a VPN Wizard option which I think was handy so I chose to go with it and change what I need after wizard sets up basics. I don’t doubt your smarts so I am going to skip over obvious screens and show you relevant screens only. First important one is where it asks for connection name and shared key. I chose to name the connection obligatory “Azure”. OBviously I won’t show you my shared key but I did paste it in the shared key field on the page. LAstly, make sure you select VPN Gateway for tunnel endpoint:
Next one is IP address of Azure gateway. Specify the IP of the Azure gateway obtained from Azure portal:
Last step in wizard is to specify IP address range of Azure VMs (it’s not 0.0.0.0 for me, it’s intentional that I’m not showing you my IP range):
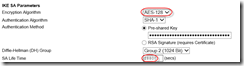
At this point the wizard is done. We need to change settings to meet Azure requirements. So I headed over to “VPN Policies” section and clicked edit for Azure policy I just created. Looking at VPN device script I had downloaded, I noticed that required encryption was AES, however, VPN wizard on FVS318 had defaulted to 3DES. So I went ahead and changed it to AES-128:
While there, I noticed that SA Lifetime was required 28800 seconds but was set to 0 bytes. Looking at the script, it was 102400000 so I changed it to match:
Next I headed over to IKE policies. Here I had to change two items. Encryption was set to 3DES, I needed to set it to AES-128. SA Lifetime was 86400 secs here so I changed it to required 28800:
The only setting from script that I couldn’t find option for was to set tcpmss to 1350. I chose to leave it alone instead of changing MTU on internet interface.
Now that the configuration is done on NetGear device, I headed over to my ISP router and configured 1:1 NAT for my dedicated IP that I had configured in Azure portal as my VPN gateway of local network. I made sure that 1:1 NAT was forwarding all traffic intended for this IP to NetGear FVS318.
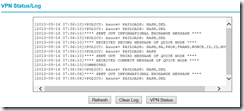
Looked like everything was configured ok and VPN should connect. So I headed over to NetGear and pulled VPN Log, which shoed me VPN was connected:
I then looked at Azure portal and it showed me that VPN connection was established:
The last thing I wanted to do to make sure everything was working as expected was to open RDP session from my Hyper-V VM to VM in Azure. All I had to do was pull up RDP client and use the IP address from my Azure VM. Everything worked as expected. Couldn’t be happier but why stop there? So I decided to change gateway in Azure to my shared IP (to see if it would have worked for you guys who don’t have dedicated IP to spare). I then created port forwarding rule on my ISP router that included UDP ports 500 and 4500, protocols AH and ESP. I already have prebuilt rule in my router so depending on your ISP router, YMMV.
And sure enough, this setup worked as well. So as long as you have UDP 500, 4500 and protocols ESP and AH forwarded to your VPN device, it seems it should work. Now I can’t tell what it will break… for example, if you are using your laptop at home to connect to work which might be using same protocols… worth thinking about and testing. I don’t have resources to test that scenario so I will leave you with two options, take a change and use shared IP NAT or dedicate an IP and use 1:1 NAT. it worked for me either way. Can’t guarantee it will for you but you now have hope since I was able to do it!
Cheers.


Great post Bhargav, nicely done. I can see you had fun writing this!